Remember when moving to the cloud promised to simplify everything? Teams sold elastic scale, lower CapEx, faster deployments — even “better security.” A few months in and you’re securing workloads across AWS, on-prem, Azure for an acquired unit and a rogue SaaS app; alerts stream from six consoles and security spend rivals compute. Welcome to hybrid cloud security.
This mess isn’t accidental—it’s what happens when cloud adoption is treated as a migration instead of a security redesign. The perimeter didn’t disappear; it multiplied. Our article breaks down the architectural choices, operational realities, and trade-offs that determine whether your hybrid environment is defensible or a disaster waiting to unfold.
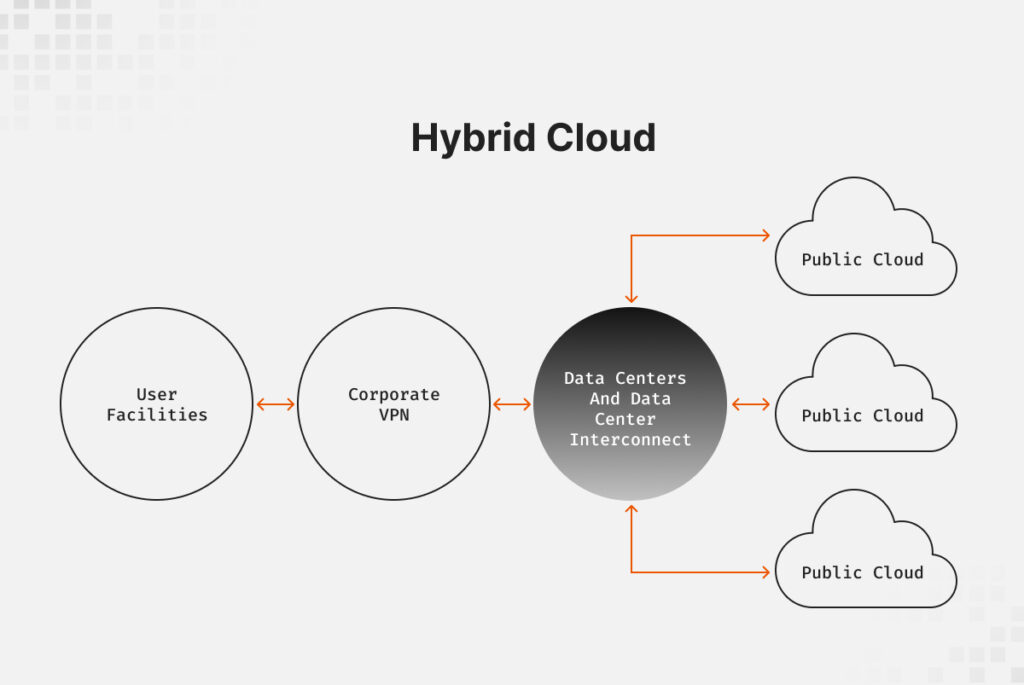
What actually happens in hybrid cloud computing environments
Let’s walk through what a real hybrid compromise looks like—not the sanitized vendor case study, but the messy, preventable reality that happens to well-funded organizations with “mature” security programs.
Week 1-3: The Silent Infiltration
Your finance department receives a convincing phishing email. One click later, credential harvesting malware is installed. Your email security gateway flagged it as “suspicious” but not “malicious.” The attacker now has basic user credentials for your on-premises network and begins systematic reconnaissance—mapping Active Directory structure, identifying privileged accounts, documenting trust relationships. Your SIEM logs this activity, but it’s indistinguishable from normal administrative behavior. No alerts fire.
Download the Hybrid Cloud Security Guide for actionable strategies.
Week 4: The Privilege Escalation
Using a known vulnerability in an unpatched domain controller (patch was “scheduled for next maintenance window”), the attacker escalates to domain admin privileges. Now they have access to service accounts that synchronize between on-premises AD and your cloud identity provider. These accounts exist specifically to bridge your hybrid cloud environment and they have elevated permissions in both domains by design.
Week 5-8: The Pivot and Lateral Movement
Here’s where traditional security models catastrophically fail. The attacker uses compromised hybrid identity credentials to authenticate to your cloud environment. From the cloud provider’s perspective, this looks completely legitimate—proper credentials, MFA satisfied through stolen session tokens, recognized VPN endpoint. Your cloud security tools see authorized access by a known account. No alerts.
Now operating with cloud admin privileges, the attacker moves laterally through your cloud workloads, accessing production databases, downloading customer data, and mapping disaster recovery infrastructure. Your cloud provider’s security services log everything but nobody correlates these cloud activities with the earlier on-premises compromise because they’re in different security consoles, monitored by different teams, analyzed with different tools.
Week 9: The Impact
The attacker deploys ransomware across your cloud infrastructure, simultaneously encrypting on-premises file shares and disabling backup systems in both environments. Only now—when business operations halt—does anyone realize you’ve been compromised for two months.
The Post-Mortem Revelation: Every individual security tool worked exactly as designed. But nobody connected the dots because the attack spanned architectural boundaries that your security program treats as separate kingdoms.
This scenario reveals why hybrid cloud environments require fundamentally different security thinking which brings us to the structural problems most organizations don’t even realize they have.
The cloud architectural flaw you inherited
The hybrid cloud security challenges of hybrid environments aren’t primarily technical. They’re structural, organizational, and economic, rooted in an uncomfortable truth most organizations avoid acknowledging.
The illusion of the unified architecture
Your organization probably describes its infrastructure as “hybrid cloud platform”, implying a single, unified architecture with consistent security controls. That’s aspirational branding, not operational reality.
What you actually have: two fundamentally incompatible security paradigms forced to coexist.
Your traditional on-premises infrastructure was built on perimeter defense: hardened network boundaries, controlled ingress/egress points, known static assets, and change management measured in weeks. Your cloud infrastructure operates on identity as the perimeter: resources that spin up and down by the hour, infrastructure defined in code repositories, security controls embedded in APIs, and change velocity measured in minutes.
These models weren’t designed to interoperate. Bridging them isn’t a matter of “integrating tools”—it requires fundamentally rethinking how you enforce policy, maintain visibility, and respond to threats across your hybrid cloud security architecture.
The federation fantasy
To enable single sign-on across your hybrid cloud environment, you implemented identity federation—probably Azure AD Connect or AWS IAM Identity Center. The promise: users authenticate once, access everything, security remains strong.
The reality: you’ve created a high-value bridge that, when compromised, gives attackers simultaneous access to both environments with the bonus that neither environment’s security tools fully understand what’s happening on the other side.
Consider what happens when an attacker compromises a federated identity. In a traditional on-premises compromise, you detect through AD audit logs, contain by disabling the AD account, and limit blast radius to on-premises assets. But federated identity compromise? Detection requires correlating events across environments (which most tools can’t do), containment requires coordinated response across domains, and blast radius is unlimited, encompassing every system trusting that identity in both environments.
The organizational divide
Even if you solve the technical challenges, you face an equally difficult organizational problem: cloud teams and traditional IT security teams operate as separate ones with different incentives, different tooling, and minimal coordination.
Your on-premises security team measures success by vulnerability reduction, patch compliance, and intrusion prevention effectiveness. Your cloud team measures success by deployment velocity, infrastructure cost optimization, and feature delivery speed. Notice what’s missing from the cloud team’s metrics? Security is often treated as a “compliance checkbox” rather than continuous operational priority.
This organizational gap creates security gaps. When cloud and security teams don’t collaborate effectively, you get cloud resources deployed without security review, security policies that work on-premises but are unenforceable in cloud, duplicate security tooling, and incident response plans that assume only one environment is compromised.
Understanding these structural flaws helps explain why hybrid cloud security consistently fails at four specific pressure points—regardless of how much money you throw at tools.
The four pressure points where hybrid cloud security actually fails
Forget comprehensive audit checklists for a moment. In practice, hybrid cloud security fails at four specific pressure points. Master these, and you’ll reduce risk. Ignore them, and every other control is theater.
Pressure point 1: The identity synchronization boundary
This is the highest-value target, so let’s get specific about what “securing the identity boundary” actually means in operational terms.
The minimum viable protection requires:
- Absolute inventory: Enumeration of every synchronized account, its permissions in each environment, and last authentication time in both. Most organizations discover they have 30-50% more synchronized accounts than they thought.
- Context-aware authentication: Basic MFA isn’t enough. You need continuous authentication evaluating device health, geographic location, time of access, resource sensitivity, and behavioral patterns. If a normally US-based account suddenly authenticates from Eastern Europe at 3 AM, that should trigger immediate verification.
- Break-glass procedures that work: When identity federation fails, you need emergency access that doesn’t require the compromised systems—cloud-native emergency admin accounts with no federation dependency, secured offline break-glass credentials, and tested recovery procedures.
- Automated hygiene: Automated deprovisioning when employees leave, permission right-sizing based on actual usage, credential rotation for service accounts, and continuous detection of privilege creep.
The test that reveals whether you’re actually secure: Can an attacker who compromises a single on-premises service account escalate to cloud admin privileges? If yes, your identity boundary isn’t secure—it’s a highway.
Pressure point 2: Log aggregation and correlation
Here’s a scenario that plays out hundreds of times monthly: an organization suffers a significant breach, hires incident response consultants, and during forensics discovers that every component of the attack was logged—they just never correlated the events.
Why correlation fails in hybrid environments: Time synchronization disasters make reconstruction impossible when on-premises logs use local time, cloud logs use UTC, and container logs have no timezone. Schema incompatibility means your on-premises SIEM expects Windows Event Logs while cloud providers send JSON-formatted events. Volume asymmetry overwhelms systems when on-premises generates 50GB daily but cloud generates 500GB. Tool fragmentation keeps GuardDuty alerts in AWS, Azure Defender alerts in Azure, and on-premises IDS alerts in Splunk. And unless someone manually checks all three consoles, multi-stage attacks go undetected.
The practical decision point: If your current Mean Time to Detect (MTTD) for multi-environment attacks exceeds 7 days, you cannot fix this with better tuning or additional analysts. You need architectural change: centralized logging that actually correlates across domains, or an MDR provider who brings their own correlation infrastructure.
Pressure point 3: Configuration drift
Infrastructure-as-code was supposed to eliminate configuration drift. In practice, it created divergence between what’s defined in code and what’s actually running.
Drift happens through emergency changes made during 2 AM incidents that never get documented, multi-environment complexity requiring coordinated updates across separate repositories maintained by different teams, cloud provider updates that change defaults without your approval, and shadow IT deploying resources that never touch your IaC pipeline.
The practical approach: Accept that 100% drift prevention is impossible. Instead, implement continuous drift detection with automated remediation—scheduled scans comparing desired vs. actual state, automated fixes for low-risk drift, alerting for high-risk changes, and quarterly reconciliation audits.
The decision trigger: If your configuration drift rate exceeds 15%, your infrastructure is ungovernable. At this point, adding more automation won’t help. You need to pause, reconcile state, and potentially engage external help to re-establish architectural control.
Pressure point 4: The incident response coordination gap
When hybrid compromise happens—and it’s when, not if—your incident response effectiveness determines whether you contain damage in hours or suffer weeks of lateral movement.
The coordination failures that extend breaches: Unclear ownership creates 45-minute delays while teams debate who’s responsible for investigating anomalous cloud API calls from service accounts. Response playbooks designed for single environments fail when compromise spans both. Communication gaps emerge when on-premises security uses ServiceNow, cloud team uses Jira, and MDR provider uses their own portal. Authority ambiguity delays critical response actions while teams seek approval for business-impacting decisions like disabling identity synchronization.
The minimum viable incident response capability: Not everyone needs a 24/7 SOC. But everyone needs pre-defined playbooks for hybrid scenarios, clear escalation and decision authority, unified communication tools, bi-annual tabletop exercises testing hybrid compromise, and automated response actions for highest-probability scenarios.
The decision trigger for MDR: If you cannot sustain 24/7 incident response—someone with authority and expertise to take action within 30 minutes, any time, any day—you cannot adequately defend a hybrid cloud environment. This is the clearest possible mandate for MDR engagement.
These pressure points reveal a harsh economic reality that most organizations eventually confront: building comprehensive internal capability is vastly more expensive and difficult than anticipated.
Final remarks: The trade-off you’re actually making
Hybrid cloud security isn’t a technical problem requiring technical solutions. It’s a strategic decision about where you allocate finite resources—time, money, attention—to maximize defensive capability.
You have three realistic options:
Option 1: Build comprehensive internal capability — Best for enterprise organizations with security budgets exceeding $5M annually.
Option 2: Accept elevated risk — Best for no one. This is the “do nothing” option that leads to breach.
Option 3: Partner with mature MDR for hybrid coverage — Best for most mid-market and many enterprise organizations.
The uncomfortable reality: most organizations claiming to “build comprehensive internal capability” are actually choosing Option 2 (accept elevated risk) because they lack the budget, expertise, or organizational capability to actually execute Option 1 successfully.
When UnderDefense talks to CISOs about hybrid cloud security, we start with a simple question: “If we simulated a federated identity compromise right now, would your team detect it within 24 hours?”
The organizations that confidently answer “yes” rarely need MDR. Everyone else should be talking to us.
Need help now?
UnderDefense’s Security Team is available 24/7. Immediate triage, containment, and forensic assistance.
1. What is hybrid cloud security?
Hybrid cloud security is the set of policies, controls, technologies, and processes that protect data, applications, and infrastructure across a mixed environment of on-premises systems and one or more public/private clouds. It ensures consistent protection while data and workloads move between environments.
2. What are common hybrid cloud security features?
Key features you’ll typically see in hybrid cloud security include:
- Identity & Access Management (IAM) — single sign-on, least-privilege roles, MFA.
Encryption — data-at-rest and data-in-transit encryption, key management (KMS). - Network segmentation & microsegmentation — isolate workloads across on-prem and cloud networks.
- Zero Trust / ZTNA — verify every user/device before granting access.
- Cloud workload protection (CWPP) — host/VM/container protection and runtime controls.
- Cloud security posture management (CSPM) — continuous configuration/compliance scanning.
- SIEM / Log aggregation & analytics — centralized logging, correlation, and threat detection.
- CASB (Cloud Access Security Broker) — visibility and control over SaaS/cloud app usage.
- WAF & API protection — protect web apps and APIs hosted across clouds.
Automated patching and configuration management — reduce surface from misconfigurations.
3. Why is security important in hybrid cloud?
Hybrid clouds increase flexibility and scale but also expand the attack surface and add complexity. Security is critical because:
- Data moves between environments — risk of exposure or leakage if not protected end-to-end.
- Inconsistent controls create gaps — different tooling/configs on-prem vs cloud lead to misconfigurations.
- Regulatory and compliance needs — data residency, auditability, and controls must be enforced everywhere.
- Increased threat sophistication — attackers exploit weak integrations or identity flaws.
Business continuity & trust — security prevents downtime, reputational damage, and financial loss.
4. What are hybrid cloud computing security services?
These are services (managed or self-managed) that secure hybrid environments, for example:
- Managed detection & response (MDR) — 24/7 threat hunting and incident response across clouds and on-prem.
- CSPM services — automated scans and remediation suggestions for cloud misconfigurations.
- CWPP / Container security services — runtime protection, image scanning, vulnerability management.
- Identity services — centralized IAM, SSO, and identity threat detection.
- Encryption / key management services (KMS) — centralized key lifecycle management.
- VPN and secure connectivity services — site-to-site VPN, SD-WAN with built-in security, private links.
- Cloud access security brokers (CASB) — monitoring and enforcing SaaS/cloud usage policies.
- Compliance & audit services — continuous compliance reporting and evidence collection.
5. What are examples of hybrid cloud security in practice?
Real-world examples include:
- Using a single IAM (e.g., corporate directory + SSO) for on-prem apps and cloud workloads with MFA enforced.
- Deploying a CSPM to scan public cloud accounts and automatically remediate risky S3/bucket or VM settings.
- Implementing microsegmentation so production workloads in the cloud cannot talk directly to management VLANs on-prem.
- Encrypting databases on-prem and in cloud and using a centralized KMS to control keys.
- A MDR provider ingesting logs from on-prem SIEM and cloud providers to detect lateral movement across environments.
- Using CASB to block risky SaaS actions (download of sensitive files to unmanaged devices).
- Deploying VPN + Zero Trust: site-to-site VPN for legacy systems plus ZTNA for remote user access to cloud apps.
6. How does Managed Detection and Response (MDR) enhance my cloud security posture?
Managed detection and response delivers 24/7 threat monitoring, detection, and active response by experienced analysts using AWS-native tools. It helps reduce dwell time, automate response, and ensure threats are addressed before damage occurs.
The post Why Your Hybrid Cloud Security Architecture is Only as Strong as Its Weakest Link appeared first on UnderDefense.