This piece compares 18 Check Point alternatives, including Palo Alto, Fortinet, Cisco, Microsoft, CrowdStrike, UnderDefense, Zscaler, Netskope, SentinelOne, Proofpoint, IBM, Cloudflare, and Imperva.
What You’ll Take Away
- A comparison of 18 Check Point alternatives with strengths and trade-offs.
- A practical PoC scorecard to verify outcomes.
- A clear operating checklist for running security on your existing tools: 360° visibility, proactive hunts, and measurable response times.
18 Check Point Competitors in 2026
- Palo Alto Networks
- Sophos
- UnderDefense
- Arctic Wolf
- Trend Micro
- CrowdStrike
- Microsoft Security (Defender + Sentinel)
- Fortinet
- Cisco Secure
- Juniper Networks
- Zscaler
- Netskope
- Akamai (Guardicore + EAA)
- SentinelOne
- Proofpoint
- IBM Security (QRadar XDR/EDR)
- Cloudflare (Cloudflare One/WAF/Bot)
- Imperva (WAF/DB/Edge)
You’ll see these 18 names recur across independent buyer guides and lab-style evaluations, e.g., MITRE ATT&CK Evaluations for enterprise and managed services, plus user-driven G2 grids for EDR and SASE/SSE comparisons.
Let’s go vendor by vendor to pinpoint the best Check Point alternative for your stack.
1. Palo Alto Networks vs Check Point
Palo Alto Networks is a top “edge-to-SOC” platform (NGFW, Prisma SASE, and Cortex XDR/XSIAM).
Strengths (why pick PANW)
- Admins often praise NGFW efficacy and the App-ID/User-ID model.
- Prisma SASE earns solid field feedback once tuned for global users.
- Cortex XDR/XSIAM unifies detection/response; some report tuning is needed to reduce noisy alerts. PoC is key.
Trade-offs vs Check Point
- Can carry higher TCO and more SKU sprawl.
- Some teams find Check Point’s SmartConsole/logging simpler day-to-day.
Pick Palo Alto if you want a single-vendor lane from perimeter to SOC with strong SASE/XDR depth.
2. Sophos vs Check Point
Sophos is an admin-friendly stack for SMB/mid-market with tight endpoint + firewall pairing (Intercept X + XGS).
Strengths (why pick Sophos)
- Often chosen for ease of use and fast rollouts, positive field notes on XG/XGS experience and support.
- MSP-friendly programs and strong endpoint tooling are common reasons teams lean toward Sophos.
Trade-offs vs Check Point
- Scales well for SMB/mid-market;
- At larger/complex estates, buyers may prefer Check Point’s unified policy/ops and prevention analytics.
Pick Sophos when simplicity, endpoint firewall cohesion, and MSP motions top the list.
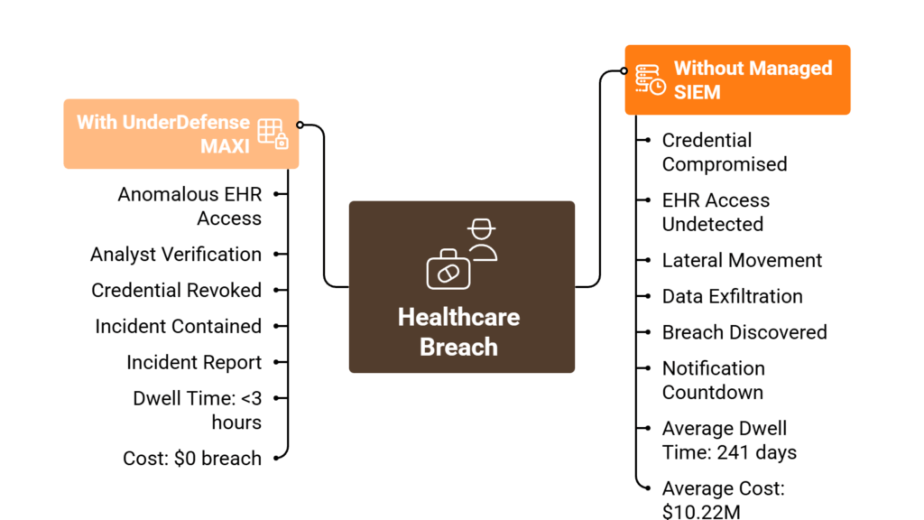
3. UnderDefense vs Check Point
UnderDefense is a services-first MDR/SOC-as-a-Service provider focused on human-led investigations, fast minutes-to-action, and operating on the tools you already own (no rip-and-replace).
Strengths (why pick UnderDefense)
- Works on your stack. Integrates with your existing EDR/SIEM/IdP and runs proactive threat hunting (hypothesis-driven hunts, anomaly baselining, and targeted sweeps) with pre-authorized playbooks.
- Speed & human judgment. Case studies emphasize measurable time-to-contain (e.g., sub-hour/minutes outcomes) and analyst-driven response.
Trade-offs vs Check Point
- UnderDefense doesn’t ship its own NGFW/SASE stack; you’ll pair its MDR with your chosen controls.
- Prove it in a PoC: like any MDR, results hinge on authority, playbooks, and minutes-to-action. Run a realistic test.
Pick UnderDefense when you want a BYO-stack, human-led MDR/SOC focused on cutting MTTR without changing your tooling.
Get Proactive SOC That Augments Your Team
UnderDefense hunts threats, responds in minutes, and protects you 24/7.
4. Arctic Wolf vs Check Point
Arctic Wolf is an MDR/SOC-as-a-Service provider with a “concierge” operating model.
Strengths (why pick Arctic Wolf)
- Hands-on guidance and run-book help; praised for helping teams improve day-to-day security maturity.
- Works across common EDR/IDP/log sources; good fit if you want MDR without rebuilding tooling.
Trade-offs vs Check Point
- Services-first scope. No native NGFW/SSE/browser controls; you’ll pair MDR with your chosen technologies.
- Outcomes depend on playbooks/authority; validate minutes-to-action and escalation paths in a PoC.
Pick Arctic Wolf when you want MDR with a guided, concierge model on your existing tools.
5. Trend Micro vs Check Point
Trend Micro is a broad platform spanning Vision One (XDR/SecOps), Cloud One (cloud & workload security), TippingPoint NGIPS (network IPS), Zero Trust Secure Access (ZTNA/Secure Web), and hosted email security, delivered largely as SaaS.
Strengths (why pick Trend Micro)
- Cloud One covers server/VM, containers, file storage, and app security in one platform. Good fit for cloud-heavy teams.
- Vision One centralizes detection, investigation, and response (now adding “agentic SIEM/SOAR” features).
- TippingPoint NGIPS for high-throughput inline protection; Zero Trust Secure Access for private and internet access control
Trade-offs vs Check Point
- Community sentiment often rates Trend’s endpoint below the very top EDRs (e.g., CrowdStrike/MDE), so run a PoC.
- If you also want best-in-class NGFW/SSE with prevention-first ops, Check Point’s platform breadth usually fits better.
Pick Trend Micro when you’re cloud-first and want Vision One + Cloud One with optional NGIPS/ZTSA and hosted email in the same vendor orbit.
6. CrowdStrike vs Check Point
CrowdStrike is a best-of-breed endpoint/XDR and managed response stack designed for fast host-level detection, containment, and threat hunting.
Strengths (why pick CrowdStrike)
- Elite endpoint + managed response. Practitioners consistently praise he value of OverWatch/Falcon Complete. They’re fast, but UnderDefense beat OverWatch by 48 hours and stopped lateral movement.
- Ecosystem-friendly. Commonly deployed alongside third-party SIEM/SOAR/IT tools.
Trade-offs vs Check Point
- Endpoint-first scope. You’ll need to assemble NGFW/SSE/email/browser with other vendors.
- Like any sensor, occasional performance or upgrade snags do show up in the wild.
Choose CrowdStrike when your top priority is endpoint/XDR excellence with proven human-led hunting/response.
7. Microsoft Security (Defender + Sentinel) vs Check Point
Microsoft Security is a broad, license-bundled stack (Defender for Endpoint/Identity/Cloud Apps + Sentinel SIEM) that fits well in M365/Azure estates.
Strengths (why pick Microsoft)
- Tight Windows/M365 integration; E5 licensing can make endpoint coverage highly cost-effective.
- Sentinel is cloud-native and flexible, with evolving cost controls and data pipelines.
Trade-offs vs Check Point
- Console sprawl/learning curve; some teams find Defender/Sentinel noisy without tuning and must mind ingestion costs.
- Check Point may be preferable when you want prevention-oriented NGFW/SSE + workspace security under a tighter, single-pane operational model.
Pick Microsoft if you’re already deep in M365/Azure and want license-leveraged XDR + SIEM.
8. Fortinet vs Check Point
Fortinet is a wide “Security Fabric” spanning NGFW + SD-WAN, FortiSASE, FortiEDR, FortiSwitch/AP for campus, and dedicated OT/rugged gear.
Strengths (why pick Fortinet)
- FortiGate + SD-WAN consolidation is a real TCO lever; admins report solid field results at scale.
- Fabric ties firewalls, switching, Wi-Fi, and rugged appliances, handy for retail/campus/industrial rollouts.
- FortiSASE for roaming users and branches; flexible when not backhauling to HQ.
- FortiEDR has fans for certain prevention/containment use cases when tuned.
Trade-offs vs Check Point
- Fabric can feel like multiple products/consoles. Many admins still prefer Check Point for unified policy + logging in one pane.
- Check Point’s prevention-first workspace/email/browser protections can feel more cohesive day-to-day for mixed-vendor environments.
Choose Fortinet when branch density and cost/perf rule.
Get the Guide to Switching Security Providers
Spot repeatable traps, stage rollback, and keep detections steady throughout.
9. Cisco Secure vs Check Point
Cisco Secure is best when networking + identity are your center of gravity (Secure Firewall, Umbrella, Duo, SecureX).
Strengths (why pick Cisco)
- Fits well if you already run Cisco networking/ISE; the pieces talk to each other.
- Duo makes MFA/ZTNA rollouts straightforward (lots of positive admin chatter).
- Umbrella adds global DNS-layer control (widely deployed; note some roaming-client gotchas to test in a PoC).
What you trade vs Check Point
- Cisco shines most when you standardize on the Cisco stack.
- In mixed stacks, many teams find Check Point faster for everyday policy edits and log digs, with richer native logging.
Pick Cisco when network integration and global DNS/MFA coverage are strategic.
10. Juniper Networks vs Check Point
Juniper is one of a network engineer’s favorites: strong routing heritage, SRX firewalls, and a powerful JUNOS CLI.
Strengths (why pick Juniper)
- SRX is praised in networking circles; great fit where routing + firewalling converge.
- JUNOS/CLI consistency across gear appeals to teams that live in CLI.
Trade-offs vs Check Point
- Security admin UX can feel CLI-first; centralized GUI/Space gets mixed reviews.
- If you want deep, prevention-first NGFW/SSE and streamlined SOC tie-ins, Check Point’s platform is usually stronger.
Pick Juniper when your team is network-heavy and wants SRX + JUNOS consistency.
11. Zscaler vs Check Point
Zscaler is an SSE/SASE cloud with ZIA (secure web/DLP) + ZPA (ZTNA), built for remote/branch users and direct-to-cloud traffic.
Strengths (why pick Zscaler)
- Mature SSE/ZTNA for anywhere users; strong global POP footprint and policy depth for web/app access.
- Popular in large remote estates; tuning matters for client behavior and split-traffic rules
Trade-offs vs Check Point
- SSE-first scope: you’ll pair with third-party NGFW and email/workspace controls.
- Admins sometimes call out portal/client complexity. Test your workflows in PoC.
Pick Zscaler when your priority is cloud-delivered SSE/ZTNA at scale.
12. Netskope vs Check Point
Netskope is an SSE/SASE platform known for inline CASB/DLP, SWG, and ZTNA. Strong on data protection for SaaS/IaaS.
Strengths (why pick Netskope)
- Data-centric SSE: respected DLP/CASB and app awareness; often wins proof-of-concepts on data protection depth.
- Good fit for SaaS-heavy estates; active roadmap and traction (recent IPO momentum).
Trade-offs vs Check Point
- As with Zscaler, you’ll assemble NGFW and some workspace controls; Check Point brings prevention-first NGFW+SSE+workspace in one lane.
Choose Netskope when SaaS/IaaS data protection (CASB/DLP) is the top as.
13. Akamai (Guardicore + EAA) vs Check Point
Akamai is strong at Zero-Trust access (EAA) and micro-segmentation via Guardicore, plus web/app security from its edge.
Strengths (why pick Akamai)
- Micro-segmentation and east-west controls to contain lateral movement; favored in complex data-center or hybrid environments.
- EAA provides VPN-less access to internal apps with granular policies.
Trade-offs vs Check Point
- You’ll manage separate pieces (EAA, Guardicore, edge/WAF); some users cite doc/community gaps and occasional stability notes. Sest at scale.
Pick Akamai when segmentation + ZTNA around critical apps is the main goal.
14. SentinelOne vs Check Point
SentinelOne is an AI-driven EDR/XDR platform (Singularity) focused on fast prevention/response with strong automation and ecosystem hooks.
Strengths (why pick SentinelOne)
- Automation-forward EDR/XDR with solid response workflows; designed to ingest native + third-party telemetry into one lake.
- Often shortlisted head-to-head with CrowdStrike; efficacy/UX vary by environment, your PoC matters.
Trade-offs vs Check Point
- Endpoint-first scope. You’ll need to assemble NGFW/SSE/email/browser controls around it.
- Like any agent/SaaS, updates/outages can bite. Plan rollback and visibility contingencies.
Pick SentinelOne when you want EDR/XDR with strong automation and API-driven response.
15. Proofpoint vs Check Point
Proofpoint is an email/security-awareness + data-protection leader with CASB/DLP options and strong people-centric controls.
Strengths (why pick Proofpoint)
- Email & DLP depth with CASB to protect SaaS use and sensitive data across channels. Good fit when email-borne risk and data exfiltration dominate.
- Widely deployed alongside M365, admins evaluate it to go “beyond EOP/Defender” in phishing/BEC scenarios.
Trade-offs vs Check Point
- You’ll pair Proofpoint with a separate NGFW/SSE/workspace stack.
- Support/false-positive frustrations do surface. Test tuning + escalation paths.
Choose Proofpoint when email/BEC/DLP is the #1 risk and you need deep people-centric controls.
Get a Tailored, Always-On Defense
UnderDefense provides 360° visibility, custom playbooks, and 24/7 response.
16. IBM Security (QRadar XDR/EDR) vs Check Point
IBM Security is a SIEM/XDR-centric approach (QRadar SIEM, QRadar EDR/ReaQta, XDR Connect) aimed at open integrations and SOC workflows.
Strengths (why pick IBM)
- SOC workflows with QRadar SIEM + QRadar EDR and XDR Connect; open integrations across EDR/NDR/SIEM.
- Identity & data. Verify (passkeys/MFA) + Guardium (discovery, monitoring, encryption).
- Exposure & response. Randori Recon (EASM) + X-Force threat intel and incident response.
Trade-offs vs Check Point
- Expect more SOC engineering to tie controls together.
- Users report sluggish UI or sizing surprises during evals. Plan capacity tests early.
Pick IBM Security when you want SIEM/XDR-centered operations with open tooling and you’ve got SOC capacity.
17. Cloudflare (Cloudflare One/WAF/Bot) vs Check Point
Cloudflare is an edge-first security platform: global WAF/DDoS/Bot, Zero Trust access (ZTNA/SWG), and SSE under “Cloudflare One.”
Strengths (why pick Cloudflare)
- Massive edge footprint; strong L7 DDoS + modern WAF/Bot controls; popular for Internet-facing apps/APIs.
- Zero Trust (ZTA/SWG) for remote/branch; often considered in SSE bake-offs alongside Zscaler/Netskope.
Trade-offs vs Check Point
- SSE/WAF-first scope. You’ll need to pair with a third-party NGFW/email.
- Client/agent and policy nuances need PoC time; Bot Management can be stringent. Test your workflows.
Pick Cloudflare for edge WAF/DDoS/Bot + Zero Trust at a global scale.
18. Imperva (WAF/DB/Edge) vs Check Point
Imperva focuses on application/data security: WAF/API, DDoS, bot mitigation, and database security.
Strengths (why pick Imperva)
- Well-regarded WAF accuracy/low false positives in third-party comps; strong for protecting business-critical apps.
- Mature database/data-layer protection story alongside app security.
Trade-offs vs Check Point
- App/data-centric portfolio. You’ll assemble NGFW/SSE and user/workspace controls.
- The operator community is smaller than “big platform” peers; plan a PoC for rule tuning and ops fit.
Pick Imperva when app/API and data-layer protection quality are paramount.
What Check Point Alternatives Must Prove in a PoC
Use the PoC to force real workloads, real users, and real incidents. Below is a tight scorecard you can run across any alternative.
|
Proof point |
How to test in PoC |
|
Minutes-to-action (MDR/SOC) |
Inject a realistic incident; time p50/p95 from alert to containment. |
|
Pre-authorized actions + rollback |
Approve sample playbooks (isolation, kill, disable account); verify audited rollback. |
|
NGFW prevention efficacy |
Run mixed traffic (apps, evasions, payloads); check TP/App-ID/IPS hit rates. |
|
SSE / ZTNA user experience |
Test roaming clients, split-tunnel, M365/Zoom; measure login/latency. |
|
Logging & investigations |
Hunt a test incident; measure search latency, pivot steps, timeline quality. |
|
Identity tie-in (IdP/SSO/EDR) |
Map IdP groups → policies; test disable/step-up MFA on signal. |
|
Email/browser protections |
Simulate BEC, credential phishing, and risky extensions. |
|
Scalability & data costs |
Push expected GB/day and users; model 12–24 mo retention. |
|
Agent performance impact |
Measure CPU/RAM/IO during scans, updates, Zoom/IDE builds. |
|
API & automation |
Build a small workflow (open/close ticket, pull evidence). |
|
Support & escalation |
Open a “brownout” ticket during PoC; measure response quality/time. |
Use this table as your live PoC scorecard. If a vendor can’t meet the bar here, they won’t meet it in production.
An Easier Way: Cybersecurity That Doesn’t Feel Complex
UnderDefense operates on the stack you already own. We help you choose the right controls, manage them day-to-day, tailor policies to your environment, and correlate signals across endpoint, identity, SaaS, cloud, and network so threats are stopped fast and noise stays low.
How do we run your defense:
- On your tools. We plug into your EDR/SIEM/IdP/NDR and wire bidirectional workflows into ITSM/SOAR.
- 360° visibility. One live picture across endpoint, identity, SaaS, cloud, and network: unified timelines, gaps flagged.
- Proactive hunts. Hypothesis-driven hunts, baselines, and targeted sweeps.
- Minutes-to-action. Pre-authorized playbooks (isolate, kill, disable, revoke, quarantine) with audited rollback.
- Identity-aware response. Actions tied to user risk, device posture, and access context.
- Cloud & SaaS hardening. Posture guardrails for AWS/Azure/GCP and major SaaS.
- Evidence on tap. Root cause, impact, actions: one export, compliance-ready.
- Co-managed or fully managed. We augment your SOC or become it — your choice.
During client onboarding, our hunts surfaced Cobalt Strike on 11 mission-critical servers. In <24 hours, we contained, cleaned, and stood up 24/7 MDR + SIEM with pre-authorized actions, cutting critical-alert response by 40% and sidestepping a ~$650K ransomware hit. See how the playbook, evidence trail, and guardrails came together — read the full case.
Get Hyper-Responsive, 24/7 Defense
UnderDefense delivers proactive hunts, minutes-to-action, and 360° visibility.
Frequently asked questions
The post 18 Check Point Alternatives: 2026 Buyer’s Guide appeared first on UnderDefense.